VPN Protocols Explained & Compared
VPN Protocols Explained
Disclaimer: While the content of this blog should be technically correct, it is addressed to a non-technical audience. As such, security experts might differ in opinion on some of the mentioned notes “if any”.
VPN Protocols Info: PPTP
PPTP stands for Point to Point Tunnelling Protocol. PPTP Advantages
- Easy to set up.
- Virtually supported on every device with VPN support.
- Low overhead and thus good speeds.
PPTP Disadvantages
- Low encryption at 128 bit. A lot of flaws were found in the MS PPTP implementation. If you are looking for security and privacy, run now :).
- Relatively unstable. If you have used PPTP before, you might know that sometimes it does take more than once to connect. And connections might drop randomly.
- Relatively easy to block by ISPs.
- NSA decrypts PPTP encrypted traffic with ease. No surprises here, given the latest security tools and cloud processing powers, any security expert worth his money probably could without too much sweat.
VPN Protocols Info: L2TP/IPSec
L2TP or Layer 2 Tunneling Protocol does not do any encryption by itself. It simply does provide the routing tunnel. VPN providers generally use IPsec for encryption. L2TP/IPSec Advantages
- Supported on most modern devices and OSes.
- Encryption at 256bit.
- Easy to set up on MAC and Windows as it is natively supported.
- No known major vulnerabilities.
L2TP/IPSec Disadvantages
- Higher encryption means more CPU, but in general, that is not a biggie for modern devices.
- Most challenging to configure on a Linux server.
- Higher encryption with double encapsulation results in B/W hit. How much depends on your device and the VPN Server/Provider.
- Relatively easy to block by ISP.
VPN Protocols Info: OpenVPN
OpenVPN is an open source application with a custom encryption protocol based on SSL/TLS key exchanges. OpenVPN Advantages
- Supports hardware acceleration with improves speeds.
- Can traverse through firewalls and NAT with great success. You can setup OpenVPN on port 443 TCP, this will make it look like HTTPS traffic and very hard to detect.
- Very stable and reliable.
- Makes use of the OpenSSL libraries for encryption. The point here is that you are running an open source application with open source maintained encryption libraries. In other words, the general public is maintaining the implementation and fixing bugs as they appear. There are no shady government agencies or suspicious design flaws.
OpenVPN Disadvantages
- Limited device support. Last time I checked there were only a handful of working OpenVPN apps for non-rooted Android and half of those did not work on all Android devices.
- If you use the default 128-bit blowfish you will get a false sense of security. So if you are setting up your own OpenVPN server change to a higher encryption protocol. If you do use OpenVPN at your VPN provider make sure they do not use 128-bit Blowfish.
VPN Protocols Info: SSTP
SSTP a.k.a Secure Socket Tunnelling Protocol uses TLS 3.0 over TCP port 443 “HTTPS” at the time of writing. This makes it secure and hard to block. SSTP Advantages
- High Encryption.
- Very hard to detect and block. It uses the HTTPS port 443/TCP this makes it easy for SSTP to traverse through firewalls and NAT.
- Supported on all Microsoft since Vista SP1.
SSTP Disadvantages
- Not supported by all VPN Providers.
- A Microsoft proprietary protocol, not available for public inspection. Microsoft is known for its security issues and cooperation with various government agencies.
- Limited support for non-MS devices.
VPN Protocol Add-Ons: TOR and Double Encryption
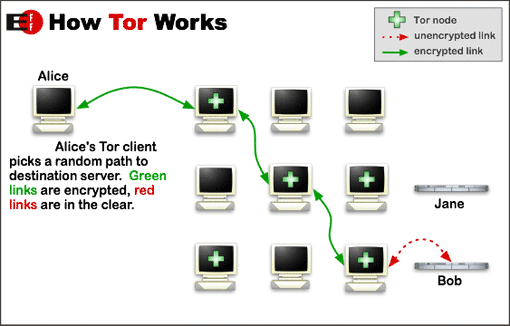
TOR: Tor is one more add-on which can be considered with and without VPN. TOR is an online free software that is designed and built to fight censorship and protect anonymity. It works by adding all the TOR users to a global network and then traffic bounces between these nodes before reaching it’s destination. Thus making it close to impossible to log and track the origin of your traffic.
Given that your traffic bounces through various nodes of other users systems and servers “albeit encrypted” it makes TOR slow. If you are paranoid though, you could combine VPN with TOR. See an illustration below on how TOR Works.
Tor Onion Network
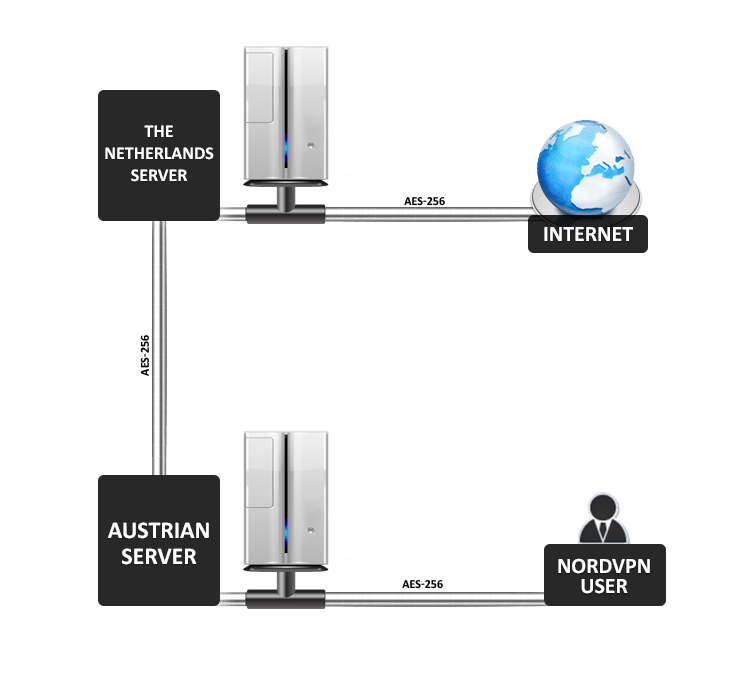
Double Encryption: Some VPN Providers have started providing Double Encryption. Where the traffic is encrypted between your PC and a VPN server, then the VPN server re-encrypts the traffic a second time over a link to a second VPN server. From there on your traffic leaves to the Internet destination. This certainly does improve anonymity, but I am a bit in doubt about the benefits of double encryption in terms of strength of data protection. See below a sample of how DoubleVPN works at NordVPN.
Double Encryption at NordVPN
VPN Protocols: Additional Considerations
Logs: Some VPN providers do keep logs, others do not. If you choose a US VPN provider it does not matter how much encryption you get, as per the PATRIOT act the VPN providers have to hand over all the info on request. If you choose a VPN provider in the EU you are slightly better of. Things are way more complicated to get to your data. The EU does put a bit more emphasis on individual privacy than the US government. If you are paranoid, you can go for a VPN provider in Panama with no VPN traffic logs, no payment logs and no valid email address needed, an example of such a provider is ExpressVPN.
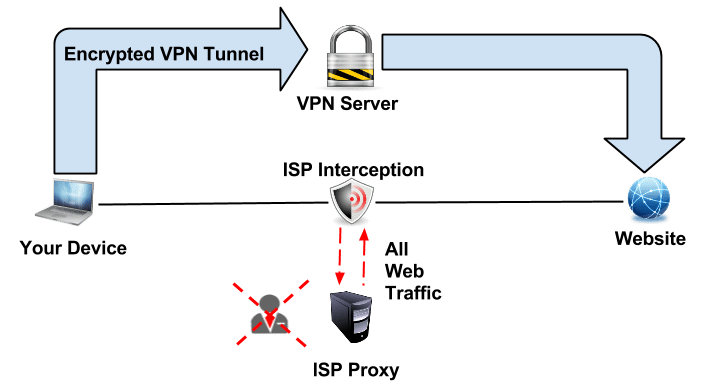
Deep Inspection: is an advanced form of pattern detection generally applied to the data section of the packets. This is used by ISPs and Governments for data mining, censorship, eavesdropping, and other uses. If you use a strong encryption protocol, your privacy is not at stake here.
However, you need to get connected to VPN first. Deep Inspection can be used to trace VPN connection attempts patters and block those connections from being established. As a result, you won’t be able to get a VPN connection to start with. OpenVPN is generally very resistant to Deep inspection given that it can run both UDP/TCP on any given port using a wide range of encryption mechanisms. For the fun of it, some of the better-known countries applying Deep Packet Inspection are :
- United States
- China
- Russia
- Iran
- Malaysia
- I am pretty sure some of the countries in GCC “UAE, KSA” do it as well, based on my ISP experience while I lived there.
VPN Protocols in Summary:
Which VPN Protocol you should use is your call. It really differs what is the best solution for you based on your needs. If all you are thinking about is getting a VOIP calls unblocked in Dubai or to watch American Netflix in Canada, then PPTP might be your thing. In case you are paranoid about your security and do want to make sure “as humanly possible on the Internet” that you are protecting your traffic, you might want to consider TOR at a VPN provider with a NO LOG policy.
If you are in a country such as Iran or China, OpenVPN might be your most stable and secure choice to overcome deep inspection. In case you are setting up your own VPN server, I hope things are a bit more understandable now. If you are looking for a VPN provider and you have set up your mind on what VPN protocols and features you need and want to check out a list of providers which lists specs per provider, please see this VPN Review site. I personally do use ExpressVPN due to their wide infrastructure and excellent support and stability, and the fact that they have easy to use and working apps for all major OSes.